Granting Automation Engine Authorizations
As an administrator, when you set up the system you create and configure User objects. On the Authorizations page you grant or deny rights to objects, files, execution data, reports, etc.
This page includes the following:
Granting/Denying Authorizations
Rights consist of access permissions and restrictions. The rights of a User are the sum of the authorizations defined on this page and on those that have been granted to the User Groups to which the User has been assigned.
Grant or deny authorizations by specifying first the objects, type of objects or groups of objects and selecting the individual rights the user should have.
-
Grp.
The Automation Engine provides 9 authorization groups that you can use to combine multiple sets of access rights. Access rights of the same group are connected via a logical OR. Access rights of different groups are connected via a logical AND.
NOT stands for access denial. It does not depend on an authorization group and applies in all cases.
-
Type
Object type (short name) to which this set of access rights applies. '*' means that they apply to all object types.
-
Name
Name of object or folder to which the access rights apply. You can also have more than one object or folder, separated by commas.
Allowed length: 200 characters.
Allowed characters: Alphanumeric and wildcard characters ("*" for any number of characters and "?" for exactly one character).
You have several possibilities:
-
Enter an asterisk *
The access rights apply to ALL objects of the type selected in the previous column (for example, to all Workflows, to all PromptSets, etc.).
-
Enter the name of just one object
The access rights apply to just this object.
-
Enter the name of multiple objects
The names of the objects must be separated by commas. The access rights apply to only these objects.
Important!
- Folder and subfolder paths must always start with a "\". For example, "\PRODUCTION\MATERIAL.HANDLING".
- When you create an object, the name of the object and/or folder you define here is compared with the name of the template object. If the names do not correspond, you are not able to create the object.
-
-
Agent*
Filter for Agent names. They are relevant for Job execution, File Transfer sources, etc.
Allowed length: 200 characters
Allowed characters: Alphanumeric and wildcard characters ("*" for any number of characters and "?" for exactly one character).
This field can also include more than one filter. In this case, they must be separated by commas.
-
Login*
Filter for names of Login objects (job execution, file transfer source, registered job output files).
Allowed length: 200 characters.
Allowed characters: Alphanumeric and wildcard characters ("*" for any number of characters and "?" for exactly one character).
This field can also include more than one filter. In this case, they must be separated by commas.
-
File Name (S)*
Filter for file names (file transfer source, registered job output files).
Allowed length: 255 characters
Allowed characters: Alphanumeric and wildcard characters ("*" for any number of characters and "?" for exactly one character).
This field can also include more than one filter. In this case, they must be separated by commas.
-
Agent (D)*
Filter for Agent names (file transfer destination).
Allowed length: 200 characters
Allowed characters: Alphanumeric and wildcard characters ("*" for any number of characters and "?" for exactly one character).
This field can also include more than one filter. In this case, they must be separated by commas.
-
Login (D)*
Filter for names of Login objects (file transfer destination).
Allowed length: 200 characters
Allowed characters: Alphanumeric and wildcard characters ("*" for any number of characters and "?" for exactly one character).
This field can also include more than one filter. In this case, they must be separated by commas.
-
File Name (D)*
Filter for file names ( file transfer destination).
Allowed length: 255 characters
Allowed characters: Alphanumeric and wildcard characters ("*" for any number of characters and "?" for exactly one character).
This field can also include more than one filter. In this case, they must be separated by commas.
-
R (Read)
Allows the user to open objects and folders. For more information, see Defining Authorizations to Folders and their Contents.
-
W (Write)
Allows the user to modify objects. This right granted for folders has the effect that a user can create objects in it.
-
X (Execute)
Allows the user to execute.
-
D (Delete)
Allows the user to delete objects and folders.
Note: Links are not objects. If a user intends to delete a link, s/he requires write access to the folder in which this link is stored. No deletion right is required.
-
C (Cancel)
Allows the user to cancel active objects.
-
S (Execution data)
Allows the user to access execution (historical) data.
-
P (Reports)
Allows the user to access the reports.
-
M (Modify at runtime)
This allows the setting of trace options on Automation Engines or Agents and the ending of RemoteTaskManager and Event objects.
* These columns are not displayed by default. To see them, click the arrow on the header row. This opens the list of available columns. The visible ones are marked with a tick, the hidden ones are grayed out. Select the one you need to make it visible; click it again to hide it.
Example
In the User object, you first define Grp. 1 to grant a user Read, Write, and Execution rights on all objects that contain TEST or PRE_PROD in their Name. Then you define Grp.2 to restrict these rights to Agent PSA only.
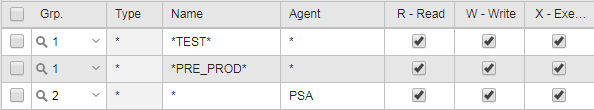
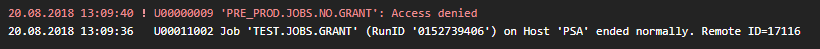
The user tries to execute the following Jobs (see Jobs (JOBS)):
-
PRE_PROD.JOBS.NO.GRANT not on Agent PSA
-
TEST.JOBS.GRANT on Agent PSA
The user is denied access to the first job, while the second job ends normally on Agent PSA:
Authorization Filters for Object Attributes
If an object's attribute (such as Login) does not contain a value (" "), the wildcard character * is used for comparison with filter lines. If an authorization line contains a particular filter for this attribute (Login), it is still checked.
Example:
The object JOBS.TEST does not contain a Login object. The following lines are still used in the authorization check:
| Grp | Type | Name | Agent | Login | File Name (S) | Agent (D) | Login (D) | File Name (D) |
|---|---|---|---|---|---|---|---|---|
| 1 | JOBS | JOBS.TEST | * | LOGIN.* | * | * | * | * |
| 1 | JOBS | JOBS.TEST | * | LOGIN.TEST.* | * | * | * | * |
Required Permissions for Predefined CA Automic Objects
To execute certain predefined CA Automic objects, additional permissions have to be set for their internally referenced Include, PromptSet, and Variable objects.
The names of these objects start with XC_. You grant Users user Read access to them by adding XC_* in the Name field and checking the box in the R column.
Defining Authorizations to Folders and their Contents
Since Folders are also objects, you can use them to collect objects and grant/deny users and user groups permissions to them at folder level.
Take the following into account when defining folder authorizations:
-
A user who has read rights on a folder can also search for that folder. That is, to be able to search for a folder it is necessary to have at least read rights on that folder.
Conversely, if a user with no rights on a folder makes a search for it via the Global Search function, the folder will be displayed on the resulting dropdown list but the user will not be able to open it or access its contents. For more information, see Global Search.
-
To filter path names, the folder must be specified relative to the top folder of the client (Root).
The filter specification starts with a "\" character. Individual sub-folders must also be separated with this character unless the wildcard character"*" is used.
If the filter ends on a "*" character, the authorizations apply for the indicated folder and all sub folders in this structure.
If the filter ends on a "\", access is only granted to the sub folders of this structure.
Authorizations given to folders are not passed on to the objects they contain.
-
Filters that include identification, directories or path specifications are displayed in the File Name (Q) and File Name (Z) fields of file transfer objects, see File Transfers (JOBF).
If "C:\TEMP\*" is specified in the File Name (Z) field , files of any name are transferred to this directory via file transfer.
-
Access modes can be determined in the fields following File Name (Z). They can also be deselected using the space bar or a mouse click.
Click Save to activate access rights or denials immediately.
Rights Applicable to Object Types
Each object type has different rights. For example, TimeZone objects cannot be executed, therefore the X-Execute right is ignored.
This table shows the rights you can use for the each object type:
| Object type | R | W | X | D | C | S | P | M |
|---|---|---|---|---|---|---|---|---|
| CALE | Y | Y | Y | Y | N | N | N | N |
| CALL | Y | Y | Y | Y | Y | Y | Y | Y |
| CLNT | Y | Y | N | Y | N | Y | Y | N |
| CODE | Y | Y | N | Y | N | N | N | N |
| CONN | Y | Y | Y | Y | N | N | N | N |
| DASH | Y | Y | N | Y | N | N | N | N |
| DOCU | Y | Y | N | Y | N | N | N | N |
| EVNT | Y | Y | Y | Y | Y | Y | Y | Y |
| FILTER | Y | Y | N | Y | N | N | N | N |
| FOLD | Y | Y | N | Y | N | N | N | N |
| HOST | Y | Y | N | Y | Y | Y | Y | Y |
| HOSTG | Y | Y | Y | Y | Y | Y | Y | Y |
| HSTA | Y | Y | N | Y | N | N | N | N |
| JOBD | Y | Y | Y | Y | Y | Y | Y | Y |
| JOBF | Y | Y | Y | Y | Y | Y | Y | Y |
| JOBG | Y | Y | Y | Y | Y | Y | Y | Y |
| JOBI | Y | Y | Y | Y | N | N | N | N |
| JOBP | Y | Y | Y | Y | Y | Y | Y | Y |
| JOBQ | Y | Y | Y | Y | Y | Y | Y | Y |
| JOBS | Y | Y | Y | Y | Y | Y | Y | Y |
| JSCH | Y | Y | Y | Y | Y | Y | Y | Y |
| LOGIN | Y | Y | Y | Y | N | N | N | N |
| PERIOD | Y | Y | N | Y | N | N | N | N |
| PRPT | Y | Y | Y | Y | N | N | N | N |
| QUEUE | Y | Y | Y | Y | N | Y | Y | Y |
| REPORT | N | N | N | N | Y | N | N | N |
| SCRI | Y | Y | Y | Y | Y | Y | Y | Y |
| SERV | Y | Y | N | Y | Y | Y | Y | Y |
| STORE | Y | Y | N | Y | N | N | N | N |
| SYNC | Y | Y | Y | Y | N | Y | Y | Y |
| TZ | Y | Y | N | Y | N | N | N | N |
| USER | Y | Y | N | Y | Y | Y | Y | N |
| USRG | Y | Y | N | Y | N | N | N | N |
| VARA | Y | Y | N | Y | N | N | N | N |
| XSL | Y | Y | N | Y | N | N | N | N |
See also: