LDAP Domain – Active Directory Security Model
Automic Automation Intelligence supports user access via LDAP domains for those environments that have LDAP servers defined. Setting up parameters for this feature is accomplished through the Administration tab - User Management Panel. The administration of LDAP servers can be very specific. Therefore consulting your LDAP administrator to properly configure LDAP domains in Automic Automation Intelligence is recommended.
This page includes the following:
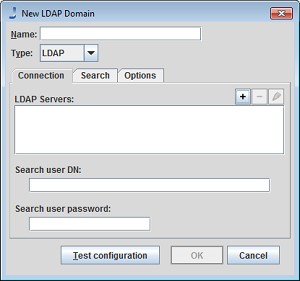
Connection Tab
-
Name: This is name the user will see in the login dialog; it has no significance outside . Must be unique.
-
LDAP Servers: A list of server: port pairs. The servers will be tried in order. The port is usually 389 (but the interface does not supply a default).
-
Search User DN: Identifies the user for accessing LDAP, by giving the complete DN for the user node.
-
Search User Password: The password for the search user.
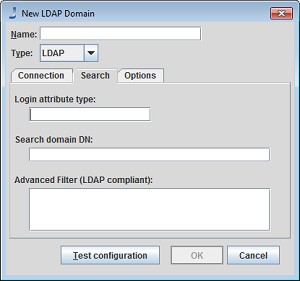
Search Tab
To look up a user in the LDAP directory, the following criteria can be used:
-
Login Attribute Type: This is the name of attribute which is used to identify users when logging in. When the user enters a user name and password, Automic Automation Intelligence searches for a node which has an attribute with this type and the user name as its value.
-
Search Domain DN: This is an LDAP DN (distinguished name), which tells where user nodes are found within the LDAP directory. All users should be found in the sub-tree identified by this name.
-
Advanced LDAP Filtering: To facilitate the LDAP domain(s) to allow logins based on groups we have added an Advanced Filter in the LDAP Domain dialog. This filter is defined according to LDAP standards.
This configuration requires advanced knowledge of LDAP. Automic Automation Intelligence will allow custom filtering of LDAP results. This helps in setting up filters to authenticate users based on certain attributes. For example, in a LDAP environment, users will have an attribute memberOf=CN=JAWSUSERS, CN=SCHEDULERS, DC=TERMALABS, DC=NET. You can put this additional filter criterion in the Advanced Filter as follows:
(memberOf=CN=JAWSUSERS,CN=SCHEDULERS,DC=TERMALABS,DC=NET)
The opening and closing parenthesis are necessary for LDAP. Automic Automation Intelligence will append this filter with & to the login attribute filter, which the user will have to specify. If you have specified the attribute as samaccountname, the filter string will look like this, if you login with username jawsuser01.
(&(samaccountname=jawsuser01) (memberOf=CN=JAWSUSERS,CN=SCHEDULERS,DC=TERMALABS,DC=NET))
The above filter will only allow users in the JAWSUSER group. Please make sure the users you are using have the attribute you are filtering on.
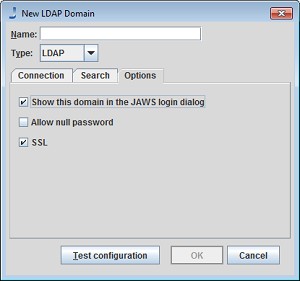
Options Tab
-
Show this domain in the Automic Automation Intelligence login dialog: If not selected, users will not be allowed to enter their password through . This is for security reasons in cases where LDAP passwords should not be handled by . In that case, users will have to login via some other method.
-
Allow null password: Unless you select this option, Automic Automation Intelligence will reject any attempt to login with a blank password.
-
SSL: To use SSL to secure user login information select the SSL checkbox. Note: the following steps will also need to be taken to fully enable SSL.
If SSL is selected for LDAP authentication then the following steps have to be taken in the Automic Automation Intelligence environment:
-
Automic Automation Intelligence needs the certificate for LDAP server. Export the certificate to a certificate file; i.e.: domain1.cer. The certificate admin should know how to do this. For a Windows 2003 server with Certification services installed take the following actions:
-
From Administrative Tools select Certification Authority. In the CA interface Expand the Certificate menu on left side. Go to Issued Certificates. Right click on the LDAP server certificate and go toAll Tasks->Export Binary Data...
-
Select Save Binary Data to file and give a file name like domain1.cer
-
-
Copy this file to the Automic Automation Intelligence server. On the Automic Automation Intelligence server run the following command:
keytool -import -v -file domain1.cer -keystore <PATH TO STORE>/jawsKeys -storepass <PASS- WORD> -noprompt
This will create a file called jawsKeys under the path specified.
Note: Repeat the above 2 steps for all the ssl ldap servers you want Automic Automation Intelligence to use. -
Modify the
.vmoptionsand add the following two lines:-Djavax.net.ssl.trustStore=<PATH TO STORE>/jawsKeys -Djavax.net.ssl.trustStorePassword=<PASSWORD>
-
Restart JBoss.
Test Configuration
Perform additional checks to determine if there is any configuration error and identify the type of error. Use this feature whenever you make changes, since subsequent login errors contain little or no information (for security reasons).
