
|
User Passwords |

Authorization System |
Configuration |

|
AE provides a client which authenticates login data using LDAP via the Microsoft Active Directory or, as of version 11 also on Oracle Directory Server. The client is part of the Automation Engine. When logging on, users are not authenticated in the Automation Engine but rather in Active Directory if the LDAP connection is activated in the User object.
The LDAP connection supports the Microsoft Active Directory and, as of version 11, the Oracle Directory Server.
As of version 11, you may synchronize LDAP data via SSL.
By default, the LDAP connection is not active.
An LDAP login via the AE is only possible, if the passwordA secret combination of characters for a Automation Engine user. includes characters of the code table you use in your respective databaseA database is an organized collection of data including relevant data structures..
A global setting activates the LDAP connection for an AE system. Whether a user is checked when logging on either locally in the AE system or via the Active Directory or Oracle Directory Server, depends on the settings made in the particular User object. Thus, AE distinguishes local and LDAP users.
Below you find the installation and configurationA set of constituent components that make up a system. This includes information on how the components are connected including the settings applied., differentiated by general setup and installation steps required either for Active Directory or Oracle Directory Server respectively.
In order to be able to use an Active Directory or Oracle Directory Server with LDAP over SSL, you will have to be able to use a JWP (Java based Work Process). Details on the installation and import of the necessary certificates you find in the JWP Installation section.
As of version 11 it is possible to have an additional LDAP technical user, who would be able to perform an LDAP synchronization, in case the current user has not the permissions to do so.
Automic recommends this method over the individual User objects solution, since in the latter case a user does not have the necessary credentials and therefore would be forced to log off the system and log in again to enable the data synchronization.
Log in and log off will not be required, if the technical user credentials solution is used.
Create a technical user by creating and using a Login object.
Follow these steps:
This Login object's credentials will be used instead of the current user's credentials for synchronizing the LDAP information.
If the key SYNC_LOGIN is not specified in the variable or the Login object does not exist, the credentials of the current user apply.
 Information stored in the User object is only updated while logging on or when using the button "Synchronize data with LDAP now". There is no automatic synchronization.
Information stored in the User object is only updated while logging on or when using the button "Synchronize data with LDAP now". There is no automatic synchronization. Logging off and in again to synchronize data is not required, if the technical user credentials solution in the special Login object (register via SYNC_LOGIN in UC_LDAP_Domain variable) is used, as described above in the "General" section.
Logging off and in again to synchronize data is not required, if the technical user credentials solution in the special Login object (register via SYNC_LOGIN in UC_LDAP_Domain variable) is used, as described above in the "General" section. The person who synchronizes the data of a User object with LDAP would also have to be an LDAP user, if the Login object solution and technical user described above is not used.
The person who synchronizes the data of a User object with LDAP would also have to be an LDAP user, if the Login object solution and technical user described above is not used.
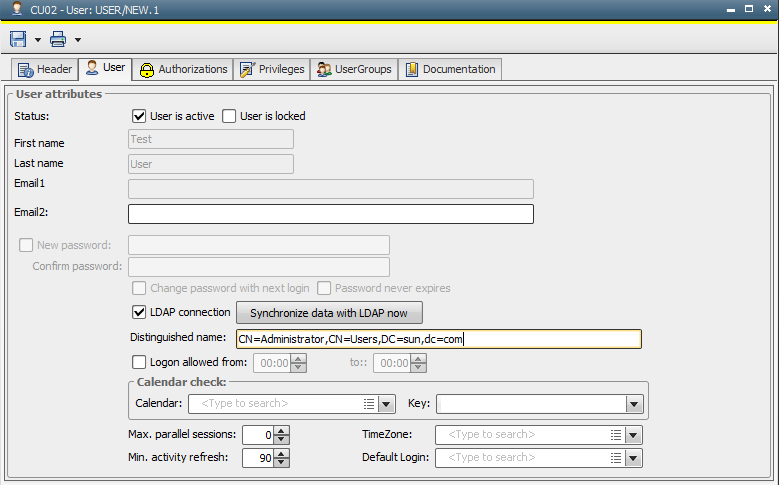
 Information stored in the User object is only updated while logging on or when using the button "Synchronize data with LDAP now". There is no automatic synchronization.
Information stored in the User object is only updated while logging on or when using the button "Synchronize data with LDAP now". There is no automatic synchronization. The person who synchronizes the data of a User object with LDAP would also have to be an LDAP user, if the Login object solution and technical user described above are not used.
The person who synchronizes the data of a User object with LDAP would also have to be an LDAP user, if the Login object solution and technical user described above are not used.The System Overview shows for each user whether or not the LDAP connection is active. You can activate or deactivate it for individual users via the corresponding context menu command.
The checkbox "LDAP connection" is automatically deactivated, if User objects are exported, transported or duplicated.
External password checks made via the AE Program Exit are called prior to the LDAP connection.
User data is stored in the object during the synchronization process with the LDAP server directory.
See also: