Installing the Agents Manually
Agents are programs that run on the target system, which can be either an Operating System or an application such as SAP, PeopleSoft, Siebel, etc. They not only establish the connection between the Automation Engine and those target systems but also start the execution of tasks and make both their monitoring and the corresponding reporting possible.
As of version 21.0, the Automation Engine and the Windows, UNIX, and Java Agents communicate using TLS/SSL. These agents establish a connection with the Java communication process (JCP), which uses trusted certificates to prove their identity to other communication partners.
Note: The TLS/SSL implementation does not apply to the HP-UX Agent, as it is no longer supported in this version.
You can use the trustedCertFolder=, agentSecurityFolder=, and keyPassword= parameters in the respective INI file to point to the relevant certificates. If the trustedCertFolder= parameter is not set, the certificates should be installed in the respective store; that is the Java trust store for Java Agents, the Windows OS store for Windows Agents, or the TLS/SSL store for UNIX Agents. For more information, see Securing Connections to the AE (TLS/SSL).
For more information about the different certificate types and for detailed instructions on how to create and use them, see What Kind of Certificates Should I Use for Automic Automation v21.
Non-TLS/SSL Agents, such as BS2000, NSK, OS/400, VMS and z/OS, still connect to a communication process (CP) and use non-TLS/SSL encryption. The communication between a TLS/SSL and a non-TLS/SSL Agent can be established using the TLS Gateway.
More information:
TLS/SSL Agents and the TLS Gateway, when used for the Automic Automation Kubernetes Edition, establish a connection to an ingress / HTTPS load balancer and not the JCP directly. The ingress / HTTPS load balancer must be reachable and requires a certificate for authentication. The address of the load balancer must be defined on both sides: the Automation Engine and the Agent / TLS Gateway.
Non-TLS/SSL Agents, when used for the Automic Automation Kubernetes Edition, establish a connection to a TCP load balancer, which must be reachable for the Agent. The address of the load balancer must be defined on both sides: the Automation Engine and the Agent.
Important! When you install or upgrade Agents manually for an Automic Automation Kubernetes Edition system, you have to make sure that you configure your Agents and/or TLS Gateway to reach the TCP or HTTPS load balancer and not the CP or JCP directly. Also, make sure that your HTTPS load balancer has the required certificates in place. For more information, see Connecting to the AAKE Cluster.
Notes:
-
Do not use blank spaces when naming the directories for the Automation Engine and the Agents. For more information, see https://support.microsoft.com/en-us/help/102739/long-filenames-or-paths-with-spaces-require-quotation-marks.
-
Check the compatibility matrix to see which version is compatible with your system. For more information, see Compatibility Information.
-
Agents running on Windows Server 2012 and higher versions: To avoid problems while executing actions (access denied), you should change the value of User Account Control: Run all administrators in Admin Approval Mode to Disabled in the
Security Settings / Local Policies / Security Optionssection of the Local Security Policy application (secpol.msc). This ensures that the Windows Agent using the local Windows administrator account (although in the administrator group) can execute actions properly.
This page includes the following:
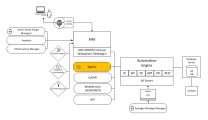
System Overview
Click the image to expand it.
Prerequisites
During a manual installation, before installing the Agents you must have installed the following components:
- Preparing the AE Database
- Installing the Utilities
- Loading the AE Database
- Installing the Automation Engine (AE)
- Installing the Online Documentation
When installing an Automic Automation Kubernetes Edition system, you must have covered the following topics:
Agent List
All agents available are listed below. To see the instructions on how to install them please click the relevant link.
See also: