Preliminary Steps
Make sure that the following conditions are met before you start provisioning an Environment:

|
The PCK.AUTOMIC_PROVISIONING Pack is installed. Note: Download the pack from https://marketplace.automic.com/. |
||||||||||||||||||||

|
Follow the steps below to recursively delete agents registered via provisioning once the Environment is deprovisioned: To Define a Recurring Execution for the Agent Remove Action
|
||||||||||||||||||||

|
The appropriate provisioning provider Pack (for example, PCK.AUTOMIC_PROVISIONING.AWS) is installed. | ||||||||||||||||||||

|
Prerequisites to provision an Environment with Amazon AWS:
|
||||||||||||||||||||

|
A new agent-client assignment object (HSTA) has been created in AE and is active. Note: The agent installed while provisioning a new Environment is auto-assigned to the current logged client in ARA. If you want to use this agent on another client you can either assign it manually or predefine the HSTA object in client 0. For more information, see Assigning Clients to Agents. |
||||||||||||||||||||

|
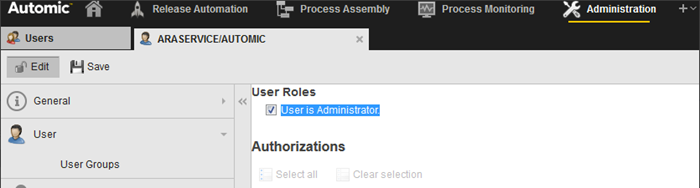
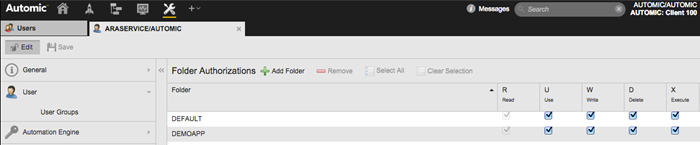
The user provisioning the Environment has been granted either:
|
||||||||||||||||||||

|
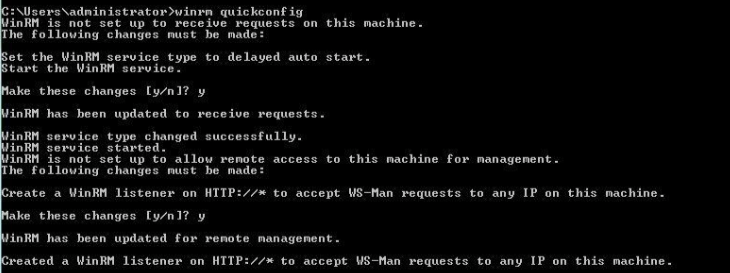
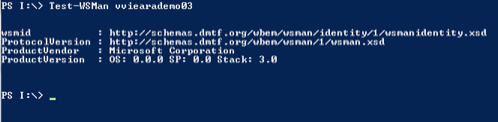
Prerequisites for Windows target boxes:
Agents running on Windows Server 2012: To avoid problems while executing actions (access denied), change the value of User Account Control: Run all administrators in Admin Approval Mode to Disabled in the Prerequisites for UNIX target boxes:
|