Granting Authorizations to Objects
On this page you grant or deny rights to work with Automation Engine objects of different types.
Rights consist of access permissions and restrictions. The rights of a user are based on an authorization profile and the authorization profiles of all groups to which the user belongs. On this page you grant or deny the user rights to objects.
Here you can grant rights for the following:
| Field/Control | Description |
|---|---|
| Grp. |
Access rights or denials are defined here. Access rights are expressed in the authorization groups 1 to 9. These groups are all on the same level. The numbers are only used to distinguish the particular groups. All access rights of the same authorization groups are connected to each other via a logical OR. Access rights defined for an authorization group thus sum up. All access rights of different authorization groups are connected via a logical AND. Only accesses for which access authorization was granted in all authorization groups are allowed. "NOT" stands for access denial. It does not depend on an authorization group and applies in all cases. |
| Type |
Particular authorizations for object types (short name) are specified here. Exception: EXTREP does not refer to an object type but to the external output of jobs. Valid object types can be directly selected from a list. If the wildcard character "*" is used, the authorizations apply for all objects and files. |
| Name | Filter for object name and folder path.
Maximum 200 characters The wildcard characters "*" and "?" can be used. "?" stands for exactly one, while "*" stands for any number of characters. This field can also include more than one filter. Several filters must be separated by commas. Folder and subfolder paths must always start with a "\". When an object is created the filter is compared with the name of the template object. If the name of the filter doesn't correspond with the template the user is not able to create the object. |
| Host | Filters for agent names (job execution, file transfer source).
Maximum 200 characters The wildcard characters "*" and "?" can be used. This field can also include more than one filter. Several filters must be separated by commas. |
| Login | Filter for names of Login objects (job execution, file transfer source, registered job output files). Maximum 200 characters The wildcard characters "*" and "?" can be used. This field can also include more than one filter. Several filters must be separated by commas. |
| File Name (S) |
Filter for file names (file transfer source, registered job output files). Maximum 255 characters The wildcard characters "*" and "?" can be used. This field can also include more than one filter. Several filters must be separated by commas. |
| Host (D) | Filter for agent names (
file transfer destination).
Maximum 200 characters The wildcard characters "*" and "?" can be used. This field can also include more than one filter. Several filters must be separated by commas. |
| Login (D) | Filter for names of Login objects (
file transfer destination).
Maximum 200 characters The wildcard characters "*" and "?" can be used. This field can also include more than one filter. Several filters must be separated by commas. |
| File Name (D) | Filter for file names (
file transfer destination).
Maximum 255 characters The wildcard characters "*" and "?" can be used. This field can also include more than one filter. Several filters must be separated by commas. |
| R | Grants Read rights.
Opening objects and folders is possible. |
| W | Grants Write rights.
Modifying objects is possible. This right granted for folders has the effect that a user can create objects in it. |
| X | Grants Execute rights.
Executing objects is possible. |
| D | Grants Delete rights.
Deleting objects and folders is possible. Links are not objects. If a user intends to delete a link, s/he requires write access to the folder in which this link is stored. No deletion right is required. |
| C | Grants Cancel rights.
Canceling active objects is possible. |
| S | Grants access to execution data |
| P | Grants access to reports |
| M | Grants Modify to Runtime rights This allows the setting of trace options on Automation Engines or agents and the ending of RemoteTaskManager and Event objects. |
Note the following for using authorization filters for object attributes: If an object's attribute (such as Login) does not contain a value (""), the wildcard character * is used for comparison with filter lines. If an authorization line contains a particular filter for this attribute (Login), it is still checked.
For example: The object "JOBS.TEST" does not contain a Login object. The following lines are still used in the authorization check:
| Grp | Type | Name | Host | Login | File name (S) | Host (D) | Login (D) | File name (D) |
|---|---|---|---|---|---|---|---|---|
| 1 | JOBS | JOBS.TEST | * | LOGIN.* | * | * | * | * |
| 1 | JOBS | JOBS.TEST | * | LOGIN.TEST.* | * | * | * | * |
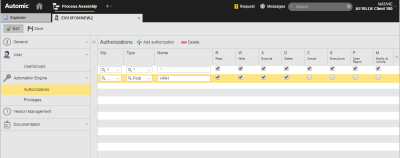
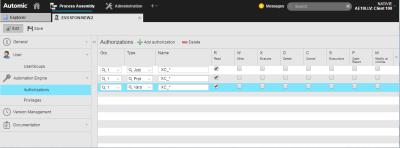
Required Permissions for Certain Predefined Automic Objects
In order to execute certain predefined Automic objects, additional permissions have to be set for their internally referenced Include, PromptSet, and Variable objects. These objects' names all start with XC_, so you can give a user read access to them by adding XC_* in the Name field and checking the box in the R column as shown below:
Definition of Rights
Several specifics apply for access rights to folders:
To filter path names, the folder must be specified relative to the top folder of the client (Root). The filter specification starts with a "\" character. Individual sub-folders must also be separated with this character unless the wildcard character"*" is used. If the filter ends on a "*" character, the authorizations apply for the indicated folder and all sub-folders in this structure. If the filter ends on a "\", access is only granted to the sub-files of this structure. Authorizations given to folders are not passed on to the objects they contain.
Filters that include identification, directories or path specifications are displayed in the fields File Name (Q) and File Name (Z) of FileTransfer objects. If "C:\TEMP\*" is specified in the field File Name (Z) , files of any name are transferred to this directory via file transfer.
Access modes can be determined in the fields following the "File Name (Z)". They can also be deselected using the space bar or a mouse click. Click Save tab in the toolbar in order to activate access rights or denials immediately.
Each object type has different rights. TimeZone objects, for example, cannot be executed. Therefore, the X right is ignored. The following illustration shows the rights that can be used for the particular object types.
| Object type | R | W | X | D | C | S | P | M |
|---|---|---|---|---|---|---|---|---|
| CALE |
|
|
|
|
||||
| CALL |
|
|
|
|
|
|
|
|
| CLNT |
|
|
|
|
|
|||
| CODE |
|
|
|
|||||
| CONN |
|
|
|
|
||||
| DASH |
|
|
|
|||||
| DOCU |
|
|
|
|||||
| EVNT |
|
|
|
|
|
|
|
|
| FILTER |
|
|
|
|||||
| FOLD |
|
|
|
|||||
| HOST |
|
|
|
|
|
|
|
|
| HOSTG |
|
|
|
|
|
|
|
|
| HSTA |
|
|
|
|||||
| JOBD |
|
|
|
|
|
|
|
|
| JOBF |
|
|
|
|
|
|
|
|
| JOBG |
|
|
|
|
|
|
|
|
| JOBI |
|
|
|
|
||||
| JOBP |
|
|
|
|
|
|
|
|
| JOBQ |
|
|
|
|
|
|
|
|
| JOBS |
|
|
|
|
|
|
|
|
| JSCH |
|
|
|
|
|
|
|
|
| LOGIN |
|
|
|
|
||||
| PERIOD |
|
|
|
|||||
| PRPT |
|
|
|
|||||
| QUEUE |
|
|
|
|
|
|
|
|
| REPORT |
|
|||||||
| SCRI |
|
|
|
|
|
|
|
|
| SERV |
|
|
|
|
|
|
|
|
| STORE |
|
|
|
|||||
| SYNC |
|
|
|
|
|
|
|
|
| TZ |
|
|
|
|||||
| USER |
|
|
|
|
|
|
||
| USRG |
|
|
|
|||||
| VARA |
|
|
|
|||||
| XLS |
|
|
|
See also:
- UserGroup Object (USRG)
- Granting Privileges to Functions