Secure the Automation Engine
This topic is an overview of the security concept used in the Automation Engine and provides descriptions or links to the detailed descriptions of all you need to do to guarantee a secure and reliable communication between all the components involved in an Automation Engine system.
An Automation Engine system consists of multiple components that are distributed among several computers and communicate with each other. For example, the Automation Engine sends the JCL to an agent which processes it on the target computer and reports back the result.
The Automation Engine can guarantee a secure communication between all the components in a system via a multi-layered security concept that involves the following:
-
Encrypting the network communication.
Encryption ensures that only the authorized communication partners can access, use or contribute to a data set and prevents potential hackers from reading or modifying transferred data. No external encryption solutions are required within an Automic environment.
See Encryption Types.
-
Defining authentication methods.
Encryption alone is not enough. It is also essential to make sure that the communication partners are not hackers. Authentication methods uniquely identify the components in an Automation Engine system.
See Authentication Methods .
- Setting Up Firewall and Port Configuration
- Deactivating the Compatibility Mode
- Changing Default Passwords
Setting Up Firewall and Port Configuration
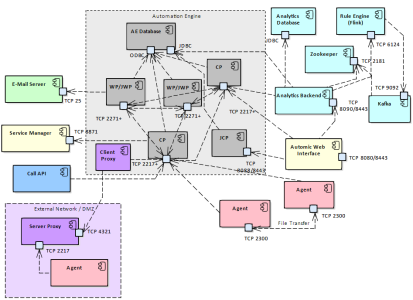
AWA requires you to have a small set of inbound and outbound TCP ports open. All ports assignments are configurable and can be changed in the configuration file of the components.
The following diagram shows an overview of all required communications and its default port numbers.
In some cases the components are distributed in different network areas, thus the following list of ports can help you with the firewall configuration.
Inbound ports
As default you need the following inbound TCP ports, nevertheless all ports are configurable:
- 2217-2221 TCP communication process (CP) of Automation Engine used by agents, user interfaces, proxy instances, etc. (The Installation Guide provides details on all these aspects.)
- 2300 TCP direct file transfers between agents
- 2271+ TCP communication of work processes (WP) (i.e. WP <-> WP and CP <-> WP)
- 8080/8443 TCP tomcat instance with deployed AWI instance
- 4321 TCP service port on client proxy
- 8090/8443 TCP Analytics Backend
- 8088/8443 TCP REST Endpoint on JCP
- 2181 TCP Zookeeper
- 6124 TCP Rule Engine (Flink)
- 9092 TCP Kafka
Outbound ports
As default you need the following outbound TCP ports, nevertheless all ports are configurable:
- 25 TCP (or access to your local email server)
- 53 TCP/UDP to DNS servers
- 4321 TCP service port to client proxy
- 8871 TCP allow start/stop of agents from user clients
File Transfers
The sending agent tries to establish a connection to the receiving agent. If this attempt fails (for example due to of Firewall settings), it notifies the Automation Engine. The file transfer request is then sent to the receiver which now tries to establish a connection to the sender. After the connection has been established, the receiving agent transfers the FT request to the sender. Thus the direction of the connection for file transfers purposes are negotiated between two agents depending on the firewall configuration.
For details on file transfers refer to the INI configuration page of the Agent Windows 64-bit.
Deactivating the Compatibility Mode
You can use "old" agent versions in later versions of the Automation Engine. For example, a 10.0.0 agent can also be used in a 11.0.0 AE system.
To be able to support agents prior to version 9.0, the Automation Engine supports unencrypted communication between components.
If you are not using these agents, make sure that encryption is enabled in your system! See Encryption Types as well as UC_AS_SETTINGS - Advanced Security for details on where and how to specify the encryption strength.
When the compatibility option is deactivated (COMPATIBILITY=NO), the Job Messenger will only accept encrypted connections. Exempted are only connections from the local IP address and the IP addresses that are defined as an exception in the Agent object. For example, when you use event monitors on z/OS in LPARs on different computers, you must enter the IP addresses of these computers in the Agent definition (see To Define the Agent-Specific Settings) The agent retrieves the list of local IP addresses from the local computer name that it obtains from the OS.
Automic recommends NOT using this setting unless you are using agents with versions prior to 9.0.
With the installation of the Automation Engine, a default user account called UC exists for client 0000. This user has full rights and privileges.
For security reasons it is highly recommended to change the default password and user name of this user.
To Change a User Password
- Login to AWI using the available UC user credentials.
-
Open the dropdown menu at the upper right corner of your application:
-
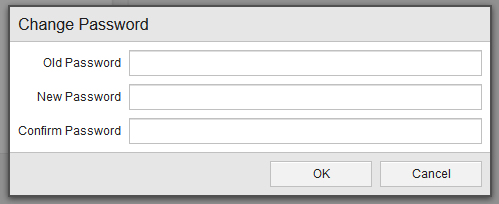
Select Change Password and fill out the fields in the following dialog as required:
See also: